Describe the Five Basic Attacks on Authentication Systems
Provide screenshots of using md5sum in your group VM under your account 5. Denial of service DoS - an attack with an intent of disrupting a network or computer to prevent other users from accessing it Retrieve from a backup - is an act of uncovering authentication database to get login information.

Top Five Worst Ransomware Attacks Social Media Infographic Cyber Attack Cyber Threat
Explain what is meant by a social engineering attack on a password.

. Retrieve from offline - Extracting information from a USB or a hard drive to gain access. Denial of services - blocking the user by either damaging the system or getting the user. A threat agent could clone or borrow a users credentials or sniff the credentials that are being transmitted.
Answers should be 3-4 paragraphs with a topic sentence that restates the question and supporting sentences using the terms concepts and theories from the required readingsEach answer should be a minimum of 300 400 words about 6 to 8 good. It is also found that a simple SQL based authentication system which is not properly architected and does not perform intelligent error handling can be vulnerable to this attack. Trial and error - an attack wherein the malicious user attempts to determine passwords or access encrypted data.
Sending passwords over all the HTTP request provides a pool of requests for attackers to pick passwords from. The 5 basic authentication attacks are Clone or borrow the credentials or token Sniff the credential Trial and error Denial of service DoS and Retrieve from a backup. The block from the account.
Describe the five basic attacks on authentication systems. The five basic attacks on an authentication system are. Describe a web-based cookie-based authentication system attack.
The attacker takes steps to enter the system so that the attack may take place. Clone or borrow is an attack that is usually done by shoulder surfing or finding the login credentials and using those to log in. Describe the three main concerns with the use of passwords for authentication.
The attacker withdraws having achieved the attacks objective. Describe the goals an ideal password authentication scheme should achieve. Artificial intelligence can automate the scanning of emails passing through the system to find anomalies such as fake websites.
An ideal password authentication scheme must withstand several types of attacks. 01032020 0920 AM Due on. Start your trial now.
Keylogger attack This is a well known type in which a Trojan is sent to users machines which sits quietly in the background and records all keystrokes. Basic Auth implemented in a non-SSL HTTPS network is a huge security vulnerabilityIt is easy to decode an Base64. Clone or borrow is an attack that is usually done by shoulder surfing or.
Describe the five basic attacks on authentication systems. First week only. They could resort to the old trial-and-error guessing or just take down the system with a DoS attack.
Outline the symmetric encryption process and explain the components involved in the process. Two-factor authentication is typically effective against these passive attacks since they include a one-time password component obtained from the device eg hardware token or phone. Explain how biometric systems are vulnerable to the five generic attacks on authentication systems.
Allows an attacker to guess a persons user name password credit card number or cryptographic key by using an automated process of trial and error. Describe the five basic attacks on authentication systems. Once they crack one the system becomes open for attacks.
Describe the five basic attacks on authentication systems. Why cant an attacker masquerade by using a hashed password. Solution for Describe an attack on a web cookie-based authentication scheme.
The attacker takes the steps needed to achieve the attacks objective. It is an upgraded version of. Describe an attack against a web cookie-based.
Describe how password hashing works a. However malware could also redirect some of those keystrokes to an attacker whom you have just enabled to log in as you. Attack types Attack description.
Describe five of these types of attacks. This by itself compromises the system by placing a malicious process within its environment. Email authentication protocols such as Domain-based Message Authentication Reporting Conformance DMARC and Sender Policy Framework SPF can help sort out the fake addresses used for impersonation attacks.
Retrieve from backup - If attackers can get their hands on this credential pattern they can next attempt to fake biometric or database credentials. Clone or borrow the credential - In this attack the credentials are duplicated and then used to log in. Write a basic C program in which a user enters the marks scored by him out of 100 in 5.
01032020 Question 00747926 Subject Education Topic General Education Tutorials. 1000 Posted By. The 5 basic authentication attacks are Clone or borrow the credentials or token Sniff the credential Trial and error Denial of service DoS and Retrieve from a backup.
Describe the five basic attacks on authentication systems Offered Price. Answers should be 3-4 paragraphs with a topic sentence that restates the question and supporting sentences using the terms concepts and theories from the required readingsEach answer should be a minimum of 300 400 words about 6 to 8 good sentences. Describe the five basic attacks on authentication systems Explain the difference between authentication and authorization.
Describe the different categories of asymmetric encryption algorithms and how they are used in practice. Summarize the different situations in which people use file encryption software.
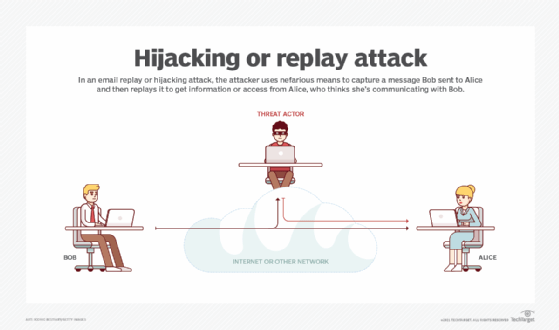
What Is An Active Attack Definition From Whatis Com

Infographic Anatomy Of A Phishing Attack Cyber Security Awareness Infographic Cyber Security Technology

Schematic Diagram Of Attack Processes Of Ransomware Download Scientific Diagram

Human Factor 2016 Infographic Cyber Security Awareness Cyber Security Computer Security

Types Of Security Attacks In Cloud Based E Learning Download Scientific Diagram

Easy Tips For Achieving Network Security Cyber Security Awareness Cyber Security Education Network Security Technology

Web Security For Your Smallbiz Liberteks Web Security Business Infographic Design Infographic

What Are Different Types Of Attacks On A System Infosavvy Security And It Management Training

Hundreds Of Businesses From Sweden To U S Affected By Cyberattack The New York Times

Buttonup Infosec Cia Triad Triad Organization Help Infographic

Advantages Of Biometric Security Biometric Security Biometrics Computer Security

Dhr International Demystifies Cyber Security Cybersecurity Infographic Cyber Security Computer Security
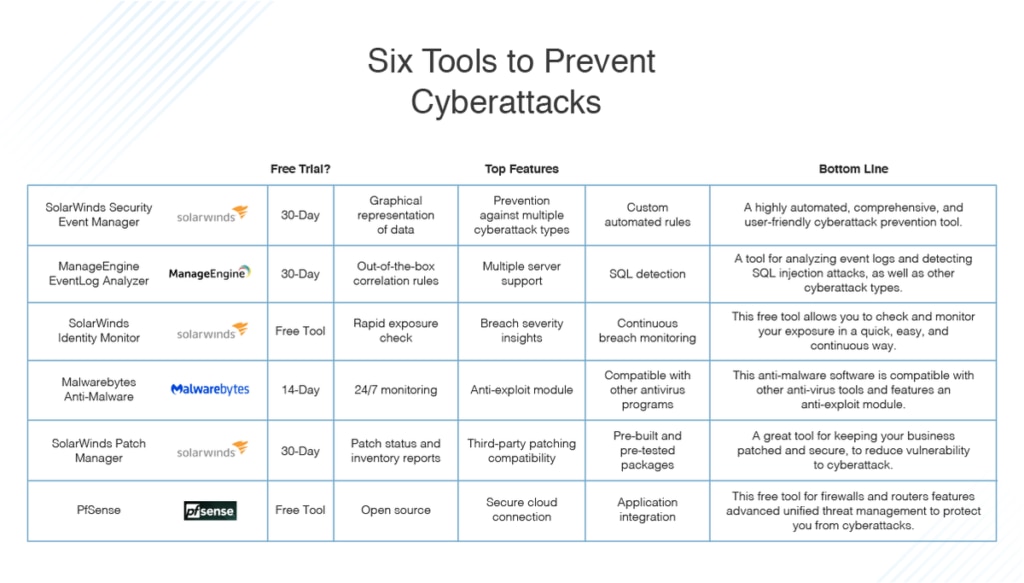
Top 6 Common Types Of Cyberattacks Dnsstuff

What Is Phishing Attack Cyber Security Education Cyber Security Awareness Computer Security

Privilege Escalation Attacks Types Examples And Prevention Purplesec
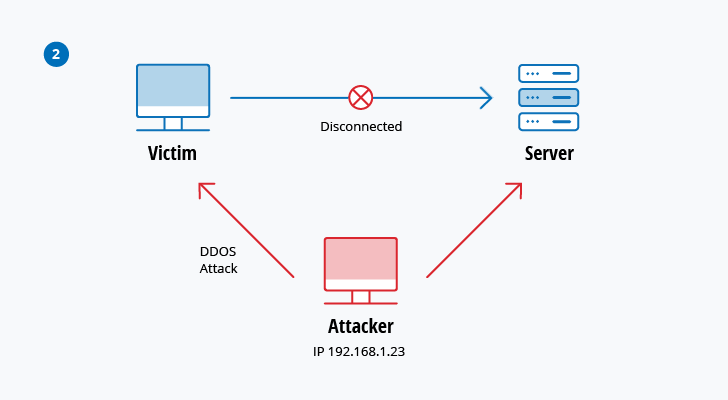
Top 10 Most Common Types Of Cyber Attacks

How To Use Public Wifi Safely Cyber Awareness Cyber Security Education Cyber Security Technology
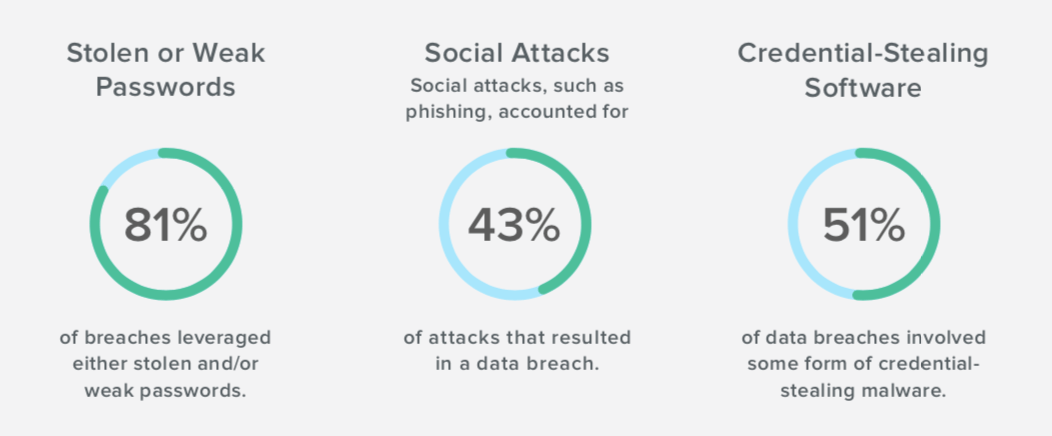
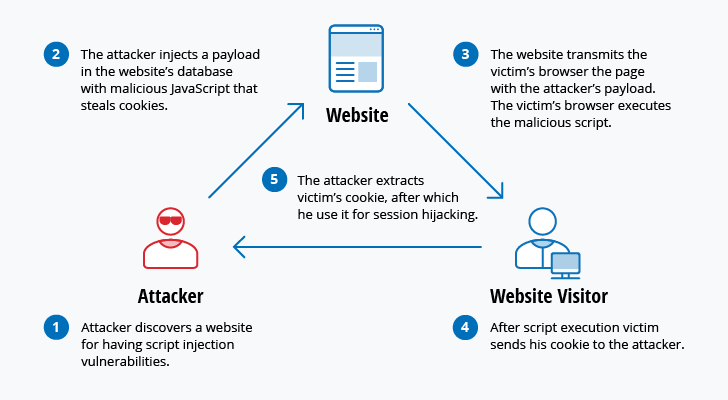
5 Identity Attacks That Exploit Your Broken Authentication Okta
Comments
Post a Comment